 It’s 4:37 a.m, I am woken up by a continuous humming noise coming from my phone. I try to ignore the unending vibrations but after gathering the courage to get out of bed, I grabbed my phone and immediately realised the vibrations where not due to the reminders set on my phone, neither were they being triggered by an active phone call, I discovered the vibrations were due to the SMSes I kept receiving continuously. The SMSes were being generated in real-time from my Online Banking Portal and the notifications kept informing me that, I had successfully logged in but had to confirm by punching in my Security (OTP) Pin (sent to my Phone via SMS) to proceed and finalise the money transfers.
It’s 4:37 a.m, I am woken up by a continuous humming noise coming from my phone. I try to ignore the unending vibrations but after gathering the courage to get out of bed, I grabbed my phone and immediately realised the vibrations where not due to the reminders set on my phone, neither were they being triggered by an active phone call, I discovered the vibrations were due to the SMSes I kept receiving continuously. The SMSes were being generated in real-time from my Online Banking Portal and the notifications kept informing me that, I had successfully logged in but had to confirm by punching in my Security (OTP) Pin (sent to my Phone via SMS) to proceed and finalise the money transfers.
I sobered up immediately but felt helpless. I knew the only thing I had to do at that time was change my Online Banking Portal Login details, unfortunately because it was that time of the day and my bank is that type of Financial Institution!, I couldn’t call them as they were closed (both their help-desk and premises) to ask them to actively monitor or tell me what was happening. Five minutes after changing the Login details, it suddenly stopped. I went back to sleep but with one eye open. I kept asking myself why it was happening to me. I went about business as usual, called my Bank around 9:00 am, they told me all was fine on their side. After pressing them for a reasonable answer they logged a call and assured me they were going to investigate.
Six hours later, my phone was back at it again! Immediately Icalled my bank again and requested them to disable my Online Banking profile as the SMSes kept coming non-stop. To cut the long story short, I decided to take the matter into my own hands and investigate why it was happening to me. I soon realised I was a victim of a “Drive-by download!” but what does that exactly mean?
A drive-by download refers to the unintentional receiving of data (downloading) of computer software from the internet to the local machine (Note: local machine can either be a computer or mobile device). The download takes place when an individual visits, surfs, browses or drives-by a compromised or malicious web page. The drive-by download can happen in two forms, that is, either an individual authorizes the download but does not understand what the implications are. In the end one ends up downloading an application that goes to installs other counterfeit or unknown software. Typical scenarios are when one visits a website that shows a pops up message reading, “We have detected that your system is not running optimally!” click on the button below to optimise your system or “A virus has been detected on your system” click the button to clean your system. Unfortunately, selecting and clicking cancel in the hope that one is closing the pop up window in some instances actually initiates a download. To make it harder for the user to ignore, these popups usually trick the user by making them believe the notifications are being generated from their current Antivirus software or Operating system. The other form, is a download that happens without the users knowledge, often a virus, trojan horse, spyware or malware is silently installed. All it takes to get infected is viewing or driving-by the infected webpage.
Drive-by download hosting websites take advantage of or exploit the visitors browser, operating system or applications. Exploits are normally present on systems with outdated software or security flaws. When an individual visits or drives-by one of these compromised websites the initial code that is downloaded is so small and is usually installed just to contact the actually machine were it pulls the rest of the ‘payload’ code from.
Of major concern is, most of these drive-by downloads are placed in normal and decent looking websites. All it takes is receiving an email, link or media post that tells one to check out an article or page on the internet. The moment one gets redirected to the compromised website, starts reading and enjoying the article, the malicious software will also be busy installing in the background. So how can one prevent against these type of attacks? The following can be useful:
- Make sure the software you are running is up to date, that is, your Operating system, applications and Internet browser including its add-ons, that is plugins & extensions.
- Make sure your browser has restrictive rights to make any changes to your machine in the event that something is downloaded. That means, running the current logged in user with limited rights. Using your browser without Administrative rights will greatly reduce the chances of getting infected.
- In the event that you prefer logging in with Administrative rights, DropMyRights application can be used to force any application to run in restricted mode.
- Use Internet search tools that warn you when you try to visit a malicious site. These features can be found in products like Eset, AVG Link Scanner or McAfee All Access.
- Run your applications, that is, web browser in a Sandboxed environment. Applications like Sandboxie will run your Web browser in an isolated space or environment which helps prevent them from making permanent changes to other programs and data on your computer.
- If you are a heavy web explorer, Security researcher or visit all sorts of sites for research purposes you might also want to boot off and browse from a Live CD or USB thatwill not allow you to make permanent changes to the Operating Systems environment. An example is Ubuntu or CentOS Desktop based disks.
- Install Internet browser addons that prevent scripts from being run from websites that you haven’t authorized. An example is NoScript if using Firefox as your browser.
- Installing Web filtering software. Web filtering software has mechanisms and capabilities to detect if a site is unsafe, once detected prevents users from going there. An example is WebSense.
- Last but not least, if at work, organisations should invest heavily in Security Awareness programs for their staff to help educate them on how to be more security conscious. Besides, all it takes for a company to be compromised is that employee who just accepts and opens any email and browses to any website.
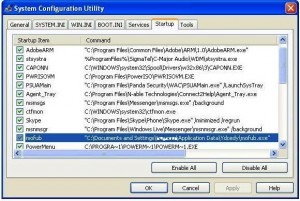
Back to my story, I discovered I had visited a drive-by download hosting website that installed a malicious spyware as seen in the screenshot above plus firewall logs which I didn’t include (let’s just say for security reasons). The Spyware had key logging capabilities and from time to time would email back all the keystrokes it had captured on my laptop to the Command and Control Center. The spyware ran every time I logged onto my PC so the fact that I had changed my password didn’t make any difference. Eventually I had to wipe clean my laptop and installed a fresh copy of Windows.
Drive-by Downloads! Gone are the days when one had to click “Accept” to unknowingly download malicious software or install malicious software before being infected, all it takes is visiting or driving-by a compromised website. Be careful where you surf online!

Dear TechnoTrev.
Thank you for the information. This is really an eye opener.
Plaxcy
It’s my pleasure Plaxcy. It’s good to know you found the article useful. Cyber criminals will stop at nothing to wipe clean anyone’s bank account. These Cyber attacks are the bank robberies of the future!
Hi Trevor, thank you for this information. I have learned a few things.
Hi Marie, it’s my pleasure. Please keep checking this site constantly for new updates